Instagram Hacking Prevention: What Top Brands Never Share
Instagram Hacking Prevention: What Top Brands Never Share
Nowadays cybersecurity isn't just important—it's essential for business survival. While most companies talk openly about their marketing strategies and growth tactics, there's a darker side to social media success that top brands rarely discuss: how they protect themselves from hackers.
With Instagram being a critical business platform, the security of your account directly impacts your brand's reputation and bottom line. That’s why we’ll share with you the protective measures that industry leaders implement but seldom share publicly.
1) Go Through Instagram's Security Checkup
Many businesses create Instagram accounts without ever reviewing their security settings. This oversight leaves your brand vulnerable to attacks that could have been easily prevented.
Security Checkup is Instagram's built-in tool that guides you through critical security steps you probably should have taken ages ago. The process helps you check recent login activity, review your profile information, confirm which accounts share your login credentials, and update recovery contact information.
While Instagram's Security Checkup covers the basics, our guide provides deeper context on why each step matters and how to implement these measures effectively. Consider this your comprehensive security roadmap that goes beyond Instagram's standard recommendations.
2) Pick A Strong Password
Your password is often your first line of defense against unauthorized access. Yet many businesses still use simple, easily-guessable passwords for their social accounts.
Here's a sobering fact: a basic eight-character password made up of only numbers can be cracked in just 37 seconds using brute force methods. Double that to 16 characters, and suddenly hackers would need 119 years to break in.
For maximum protection, create randomly generated passwords that are at least 14 characters long and include numbers, special characters, and both upper and lowercase letters. According to Hive Systems, such passwords would take hackers approximately 805 billion years to crack through brute force methods.

Also, avoid the common mistake of password recycling. A Google study found that 65% of people use identical passwords across multiple accounts. If hackers breach one of your accounts, they'll immediately try those same credentials on your other platforms.
The simplest solution is to use a password manager to generate, store, and autofill strong, unique passwords for all your accounts.
3) Enable Two-Factor Authentication (2FA) For Teams
Two-factor authentication adds a crucial second layer of protection by requiring both your password and a time-sensitive code that changes every ~ 30 seconds.
While 2FA is essential, traditional implementations create headaches for brands with multiple team members managing social accounts. Standard 2FA typically links to a single device or account, forcing team members to contact the main administrator for access codes.
This creates needless friction and delays. Instead, implement team-based 2FA that allows multiple authorized users to access a single account with regularly changing verification codes.
The major advantage of team-based 2FA is access management. When employees leave your company, you can instantly revoke their access through your dashboard without changing passwords or disrupting other team members.
While several platforms offer 2FA capabilities, we recommend exploring Spikerz and its comprehensive account protection toolkit for the most robust solution.
4) Enable Login Requests
Login requests provide real-time oversight of who's accessing your account and from where.
When you set up two-factor authentication on Instagram, you'll automatically receive alerts whenever someone attempts to log in from an unrecognized device or browser. These notifications include details about the device and its location.
You can immediately approve or deny these login attempts directly from your currently logged-in devices, maintaining complete control over account access.
For ongoing monitoring, you can review recent login activity at any time by navigating to "Settings," then "Security," and "Login Activity." If you spot a suspicious login, you can log out that device and report the unauthorized access to Instagram.
5) Update Your Phone Number And Email
Make sure the email and phone numbers associated with your account are up-to-date and accessible. This allows Instagram to contact you about important security issues or account recovery.
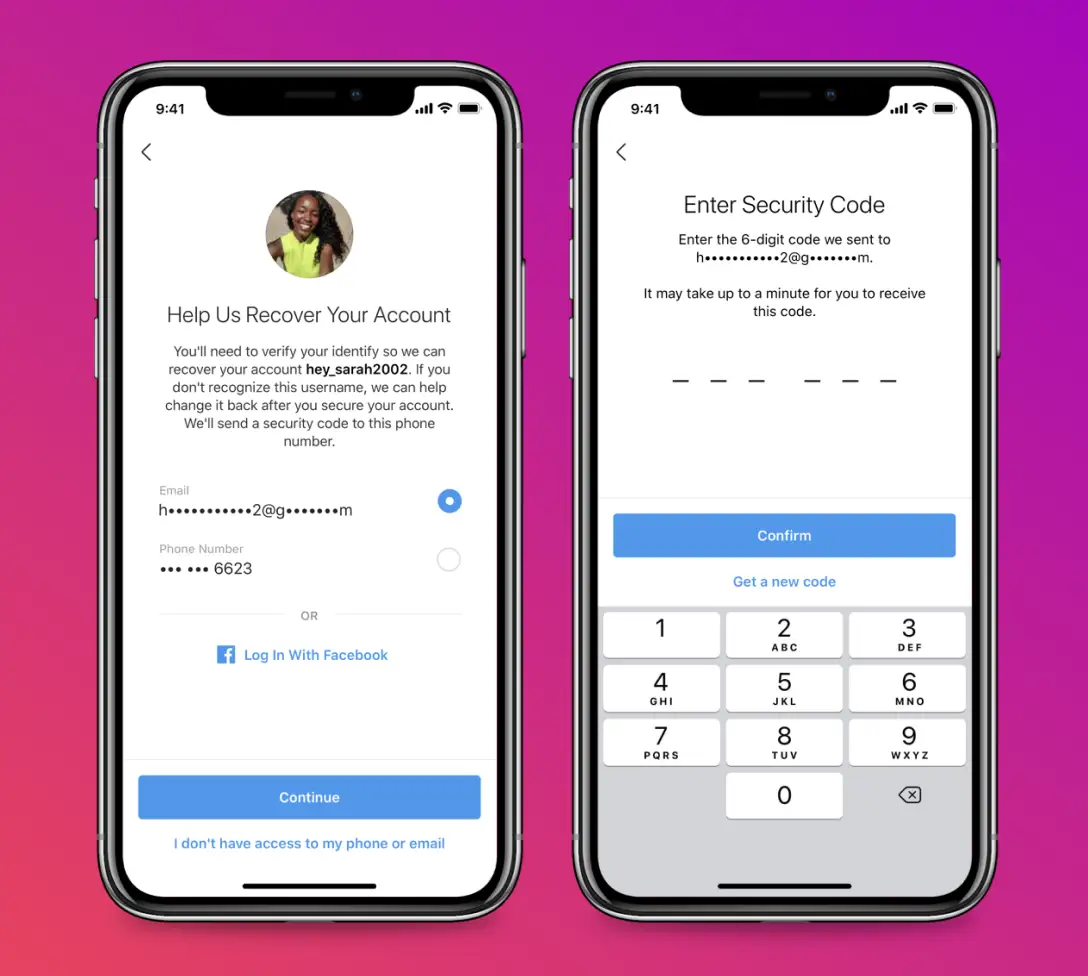
However, we recommend only using your phone number for contact purposes, not for authentication. Phone-based verification can be compromised more easily than other security methods, so it's better to rely on multiple protection layers spread across separate devices.
6) Report Content And Accounts You Find Questionable
Brand impersonation has become increasingly sophisticated, making vigilant monitoring essential to protect your reputation.
Implement comprehensive social listening and narrative monitoring across all digital channels—social media, news sites, dark web forums, chat platforms, and more. This vigilance helps identify brand abuse before it spreads.

The strongest protection comes from legally registering all your trademarks, logos, and brand assets with appropriate authorities in every market where you operate.
Continuously monitor social media for impersonating accounts and content theft. When you discover someone misusing your brand assets, report them immediately through Instagram's reporting tools.
You can report individual content by tapping the three dots above a post, holding on a message, or visiting an account profile and reporting directly from there.
7) Use A Social Media Security Tool To Protect Your Accounts
While built-in platform security features provide baseline protection, dedicated security tools offer comprehensive coverage that addresses multiple vulnerabilities.
Social media security tools are specialized applications that monitor your accounts for suspicious activities like unauthorized login attempts, unexpected profile changes, or mass content deletion.
These tools automatically flag suspicious messages, eliminating the need for manual verification. They shield your login credentials and sensitive information from malware and keyloggers designed to steal data.
If a breach occurs, they provide step-by-step recovery guidance to quickly regain control of your account.
Consider Spikerz as an example of what these tools can offer. Spikerz identifies brand impersonators attempting to spread misinformation, scam your audience, or damage your reputation. It prevents phishing attacks by detecting suspicious messages and links—even those appearing to come from trusted sources.

Spikerz also helps prevent account hijacking, alerts you to data breaches involving your business information, analyzes content before publishing to avoid shadowbans, removes bot accounts from your audience, and automatically backs up your content so nothing is permanently lost if your account is compromised.
If you are not already using a social media security tool to protect your social media accounts, consider using one today.
8) Educate Your Staff On Cyber Security
The human element remains the weakest link in most security systems, with phishing attacks being the most common entry point for hackers.
Train your employees to recognize online threats and respond appropriately when facing targeted attacks. Schedule regular training updates to keep the team informed about evolving cyberattack trends and prevention techniques.
Remember that modern phishing attempts often look identical to legitimate communications, sometimes even displaying fake security indicators that typically denote safe sites.
Establish a clear policy: if employees didn't initiate the communication, they should never provide sensitive information, regardless of how authentic the request appears.
9) Create A Social Media Policy
Formalized guidelines prevent security lapses and maintain brand consistency across all team interactions.
A social media policy provides clear guidelines for employees posting content online, whether professionally or personally. This document should outline password security requirements, mandatory use of two-factor authentication, brand voice guidelines, role definitions, security protocols, and other relevant standards.
This policy creates accountability and ensures all team members understand their responsibilities in maintaining your social media security.
10) Create A Crisis Management Plan
Even with strong preventive measures, security incidents can still occur. Preparation makes the difference between a minor disruption and a major crisis.
A crisis management plan outlines exactly how your business will respond if a security breach or a PR issue happens. The plan should clearly identify who takes action and define their specific roles. The goal is minimizing damage and restoring normal operations as quickly as possible.

While plan formats vary, most effective crisis plans function as actionable checklists. When problems arise, your team can systematically work through predetermined response steps rather than making panic-driven decisions.
11) Authorize Third-Party Apps Carefully
Third-party applications can provide valuable functionality but may also create security vulnerabilities if not properly vetted.
Exercise caution when authorizing any third-party app to access your Instagram account. Never share login credentials with applications you don't fully trust.
When you grant access to these apps—whether through API tokens or direct username/password sharing—you're potentially giving them complete control over your account. Always research applications thoroughly before connecting them to your business profiles.
Important Things To Know
Beyond implementing protective measures, understanding common attack vectors and having a response plan are crucial for comprehensive security. Here are additional critical insights that can help you avoid getting hacked and guide your response if an incident occurs.
Instagram Will Never Send You A Direct Message (DM)
One of the most common Instagram scams involves fake direct messages claiming to be from the platform itself.
Malicious accounts frequently send messages claiming your account is at risk of being banned, that you're violating intellectual property policies, or that your photos are being shared without permission. These messages attempt to trick you into providing sensitive information like passwords.
Remember this absolute rule: Instagram will never contact you through direct messages. All official communications come through the app's notification system or your registered email. When Instagram identifies these scams, they take action—but you should immediately report such content and block the sending account.
What To Do If You Get Hacked
If you discover someone has gained unauthorized access to your account or you're unable to log in, take immediate action. Visit Instagram's dedicated hacked page from your desktop or mobile browser to begin the account recovery process. The system will guide you through verification steps to regain control.
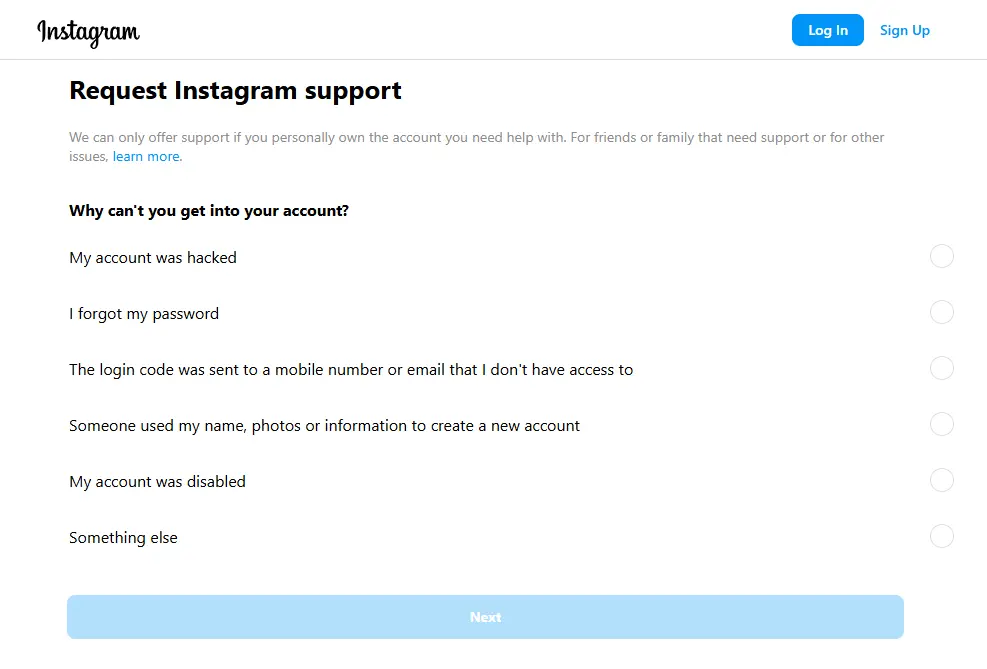
Also, immediately secure your email account, as anyone with access to your email can likely access your Instagram account as well. Change your email password and enable additional security features before attempting to recover your Instagram profile.
Conclusion
The security of your Instagram account directly impacts your brand's reputation, customer trust, and business operations. While implementing robust security measures requires initial effort, the protection they provide far outweighs the potential costs of a breach or account hijacking.
Remember that security isn't a one-time setup but an ongoing process requiring vigilance and adaptation. Regularly review your security practices, stay informed about emerging threats, and ensure your entire team understands their role in maintaining your online brand safety.
The most successful brands on Instagram aren't just those with the best content—they're those who have built an invisible fortress around their digital presence. Don't wait until after an incident to prioritize security.
The protective measures outlined in this guide represent hidden practices that top brands implement but rarely discuss publicly. By adopting these security protocols today, you position your business to thrive on Instagram without the looming threat of security breaches undermining your hard-earned success.














