Why Hackers Target SMBs First (And How to Stop Them)
Small and medium-sized businesses are always prime targets for hackers. Why? Because they often have valuable data but fewer security resources than larger companies. This security gap creates a perfect opportunity for cybercriminals looking for an easy score.
The impact of these attacks can be devastating. When hackers breach digital assets like social media accounts, they damage brand reputation, steal customer information, and potentially cripple business operations.
The good news? Most of these attacks exploit predictable security blind spots that you can fix once you know where to look.
In this blog post, we’ll examine why SMBs are vulnerable, what threats they face, and the practical steps you can take to protect your business's social media presence and digital assets.
Why SMBs Are Easy Prey for Cybercriminals

Cybercrime is big business. According to Statista, cybercrime costs in the United States reached an estimated 452.3 billion U.S. dollars in 2024. This number is expected to skyrocket to approximately 1.82 trillion U.S. dollars by 2028.
So why do hackers set their sights on smaller businesses? The answer is simple; it’s your security gaps.
1) Limited Security Tools
Many SMBs rely on free or consumer-grade cybersecurity tools instead of business-focused solutions, leaving critical vulnerabilities that targeted tools would address.
2) Insufficient Training
Employees at SMBs receive less cybersecurity training, making them more likely to fall for scams, click malicious links, or reveal sensitive information. According to the 2024 Verizon DBIR, only 1 in 5 people successfully recognize and report a phishing attack when they encounter one.
3) Lack of Awareness
Some SMBs don't fully understand the risks or importance of cybersecurity, leading to inadequate protective measures.
4) Attractive Target Profile
Hackers view SMBs as easier to exploit and less likely to have resources to recover from a breach or track them down.
5) Resource Constraints
Smaller budgets and fewer IT staff compared to larger organizations mean SMBs often lack specialized cybersecurity expertise, creating blind spots in threat detection and response.
Which Types Of Cyberattacks Are SMBs Most Exposed To?

Small businesses face many cyber threats daily. Understanding what you're up against is the first step toward protecting your digital assets and social media accounts. Here are the most common threats SMBs face:
Phishing: The Most Common Form Of Malware Attack
Phishing is the most common form of cybercrime, with an estimated 3.4 billion spam emails sent every day. These attacks trick users into revealing sensitive information like usernames, passwords, addresses, and payment details.
Hackers use email and social media to manipulate users through fear-based messaging, fake rewards or deals, and convincing website replicas designed to harvest credentials.
What makes phishing so dangerous for SMBs is its efficiency and effectiveness. Attackers can send millions of emails at almost no cost, needing only a small percentage of successful compromises to profit.

A staggering 64% of businesses report facing Business Email Compromise (BEC) attacks in 2024, with average losses of $150,000 per incident. Around 80% of phishing campaigns aim to steal credentials for cloud services like Microsoft 365 and Google Workspace, which are the backbone of most small business operations.
Also, the human factor amplifies this risk. SMB employees often juggle multiple responsibilities under time pressure, making them more likely to click hastily on malicious links. Combined with a lack of clear procedures for verifying unexpected requests for sensitive information, this creates a perfect storm of vulnerability.
Viruses: Infecting Local Devices
A virus is a malicious program designed to damage computer systems by altering software, corrupting data, or causing harmful actions. According to the 2024 Verizon DBIR, 94% of malware arrives through email attachments. Once inside your system, malware can steal sensitive information, lock up critical systems, and provide backdoor access to hackers. The damage often occurs before you even realize you've been compromised.

SMBs are particularly vulnerable because they typically delay software updates due to cost concerns or fear of operational disruption. Without dedicated IT security staff to monitor systems, small businesses often rely on basic consumer-grade antivirus rather than complete endpoint protection. This creates significant gaps in your defense that sophisticated malware can easily exploit.
Insider Threats: Cyber Espionage
Insider attacks happen when employees use their legitimate credentials to access sensitive areas of your network for malicious purposes. These might be disgruntled workers, profit-seekers, or those involved in cyber espionage.
What makes insider threats especially dangerous is their potential for catastrophic damage. They can easily cripple your company because employees already have access to customer payment information, company data, and sensitive communications.
Suspicious activity from legitimate accounts using proper credentials is much harder to detect than external attacks, particularly since SMBs typically don't implement user activity monitoring or advanced threat detection systems.
Also, many small businesses maintain loose permission structures where employees have access to more systems and data than necessary for their roles. Access often isn't quickly revoked when employees leave the company, creating another vulnerability. Additionally, small teams frequently share passwords for convenience, creating security risks and making it difficult to trace the source of breaches when they occur.
Ransomware: Taking Your Accounts Hostage
A ransomware attack occurs when hackers take control of computers or servers, lock users out, and demand payment before restoring access. That said, the biggest problem is that even if you pay, there's no guarantee you'll regain control.

According to Statista, ransomware infections primarily spread through phishing (54%), followed by poor user practices and gullibility (27%), lack of cybersecurity training (26%), and malicious websites (14%). This multi-pronged attack vector makes ransomware particularly difficult to defend against without comprehensive security measures.
SMBs are particularly attractive ransomware targets for several reasons. For example:
- They often lack proper, air-gapped backup systems that would allow recovery without paying the ransom.
- Many find paying the ransom cheaper than rebuilding systems or suffering extended downtime.
- Attackers know SMBs face existential threats from extended outages and often lack cyber insurance, making them more likely to pay up quickly.
- Most SMBs don't have developed plans for operating during system outages, making recovery even more challenging.
DDoS Attacks: Denial of Service
A Distributed Denial of Service (DDoS) attack aims to make your website or online services unavailable by overwhelming them with traffic from multiple sources.
DDoS attacks are particularly problematic for SMBs because they immediately take websites and services offline. Attackers often use DDoS as a smokescreen while conducting more sophisticated attacks elsewhere in your system. Since SMBs depend heavily on their websites for customer interaction, this downtime can be particularly damaging to both operations and customer trust.
The technical architecture many small businesses use adds to their vulnerability. Many use shared web hosting, meaning a DDoS attack on one site affects all customers on the same server. When these attacks occur, they can significantly impact an SMB's operating budget, revenue, and customer relationships, often with long-lasting consequences.
Botnets: Compromising Multiple Targets
A botnet is a network of infected internet-connected devices controlled remotely by hackers to execute large-scale cyberattacks.
Botnets provide attackers with distributed computing power for various malicious activities. They enable criminals to execute campaigns through compromised devices, creating several layers of separation between themselves and the actual attack. What makes botnets particularly dangerous is their versatility – a single botnet can simultaneously send spam, launch DDoS attacks, mine cryptocurrency, and distribute ransomware.
SMBs are vulnerable to botnet infiltration because they typically lack the tools to detect unusual outbound traffic that would indicate botnet activity. Many implement IoT devices without proper security measures, creating prime targets for botnet recruitment. Without security expertise, small businesses often miss early warning signs of infection, allowing the botnet to operate undetected within their systems for extended periods.
Cybersecurity Best Practices That Won't Break Your Budget
Protecting your SMB doesn't require enterprise-level resources. If you implement these practical security measures, you’ll significantly reduce their vulnerability to cyber threats and safeguard your social media presence.
1. Perform a Security Assessment
A security assessment is an honest, transparent analysis of your network defenses' strength. It involves identifying potential vulnerabilities, including employees, applications, and practices that weaken your security posture.
For SMBs, security assessments provide a structured approach to identifying and addressing vulnerabilities before exploitation. They help identify the most critical areas for maximum impact with limited resources, costing far less than recovering from a breach. These assessments categorize vulnerabilities by severity, allowing you to address critical issues first within budget constraints.
A good assessment delivers a clear, actionable security improvement plan rather than attempting to implement everything at once. It identifies critical systems and data requiring protection and backup, ensuring business continuity even if a breach occurs. Perhaps most importantly for SMBs, assessments evaluate vendor security practices, addressing a common vulnerability point for smaller organizations that rely heavily on third-party services.
Do you need help performing your security assessment?
Get a free security social assessment from Spikerz and know exactly where you stand. Discover your weaknesses and learn how to defend against hacks, phishing, and content violations that can get you banned. Click here to schedule your free assessment now.
2. Train Your Employees
Employee cybersecurity training provides your team with the knowledge and skills to recognize and respond to threats effectively.
According to the 2024 Verizon DBIR, the human element is involved in 68% of breaches. Of those, 80-95% begin with a phishing attack. Even more alarming, according to SlashNext, the total volume of phishing attacks has increased by 4,151% since ChatGPT's release in 2022.

Training delivers exceptional ROI for SMBs because it transforms employees from your biggest vulnerability into a central part of your defense. It teaches staff to recognize threats, respond appropriately, and understand their role in prevention and recovery. Creating this human firewall provides one of the highest returns on security investment, establishing a significant security barrier at relatively low cost.
Well-trained employees act as an additional security layer, multiplying the effectiveness of technical controls you've implemented. Their knowledge leads to stronger password practices and proper credential management throughout your organization. Employees who understand security risks are less likely to implement unauthorized solutions that create vulnerabilities, and they'll improve security practices on personal devices that may access company systems.
3. Use Antivirus Software And Keep It Updated
Antivirus software prevents, detects, and removes viruses and other malware from your networks, computers, and devices.
For SMBs, quality antivirus provides an essential protection layer against diverse threats that would otherwise slip through. Top-tier solutions, when kept updated, ensure the latest protection against recent attack types that basic security can't detect. These updates include patches for newly discovered vulnerabilities, protecting you before official system patches become available.
Modern antivirus offers continuous, automated monitoring without constant human intervention, perfect for businesses with limited IT resources. It helps secure various endpoints outside the traditional network perimeter, an increasingly important consideration with remote work.
Today's advanced solutions provide real-time protection against malicious websites and downloads, with specific protections against ransomware that can save your business from catastrophe. As an added benefit, modern tools provide valuable data about attempted attacks, helping you understand your threat landscape and adjust your security posture accordingly.
4. Secure Your Networks to Protect Sensitive Data
Network security is foundational because networks serve as the primary infrastructure through which sensitive data flows.
For SMBs, proper network security ensures only authorized users with proper credentials can access sensitive data and devices. Since networks provide pathways to all business data and systems, securing these creates a strong first defense line before attackers can reach valuable assets. Properly secured networks significantly reduce potential attacker entry points, making your business a less attractive target.
Network-level security is often more cost-effective than securing each individual endpoint or application–an important consideration for budget-conscious SMBs. Properly configured firewalls, network segmentation, and access controls prevent unauthorized system access, while encryption protects data both at rest and in transit, making it unusable even if intercepted. Network-level security can also detect and block malware attempting to spread between systems or communicate with command and control servers, containing potential breaches before they escalate.
5. Use Strong Passwords
Passwords are the primary authentication barrier between attackers and your sensitive data and systems.
For SMBs, implementing strong password practices starts with creating randomly generated passwords with at least 14 characters long. These should use a mix of numbers, special characters, and uppercase and lowercase letters for maximum security. According to Hive Systems, this combination would take hackers approximately 805 billion years to crack through brute force methods, providing excellent protection at no additional cost.
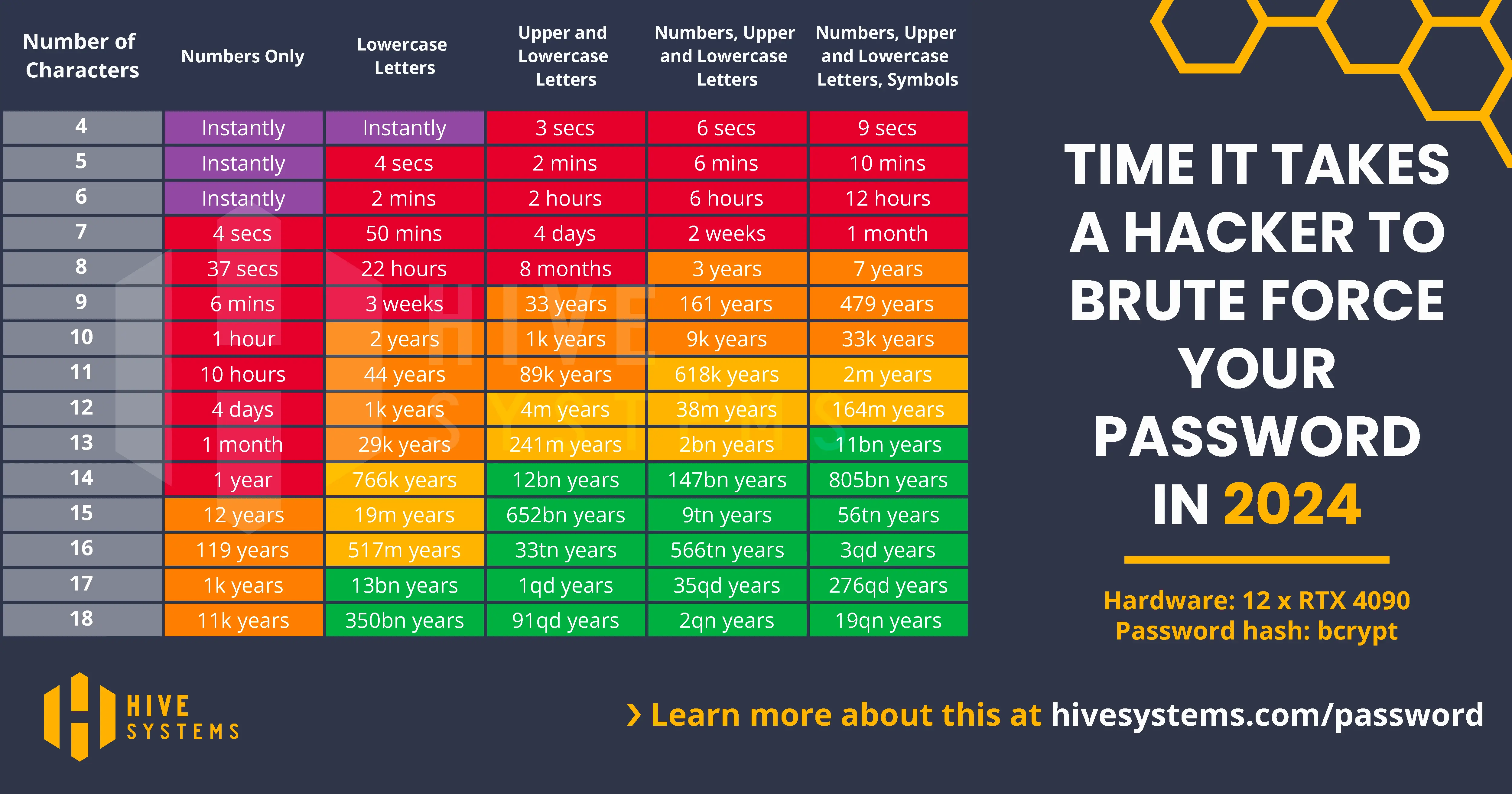
Avoid password recycling across different platforms to prevent cascade breaches where one compromised account leads to multiple systems being compromised. Implementing strong password policies also helps meet regulatory requirements like PCI DSS, HIPAA, and SOC 2, which may be necessary for your business operations and client relationships.
6. Set Up Multi-Factor Authentication
Multi-factor authentication (MFA) requires users to provide two or more verification factors to access systems or accounts.
For SMBs, MFA ensures only legitimate users gain access regardless of connection location. It significantly reduces phishing effectiveness since attackers need both the password and physical access to the second authentication factor, dramatically increasing their challenge. MFA particularly improves security for high-value administrator accounts with extensive system access, protecting your most critical system privileges.
The value of MFA is widely recognized in the security community – 87% of firms with over 10,000 employees use MFA. However, it's important to note that despite its effectiveness, 28% of MFA users are still targeted through sophisticated tactics like SIM-jacking, MFA Hammering, and AiTM Attacks. This reinforces the need for a layered security approach rather than relying on any single protection.
7. Back Up Your Data
Data backup involves creating copies of important information and storing them separately to protect against loss.
For SMBs, proper backups ensure business continuity despite cyber incidents, hardware failures, natural disasters, or human error. Properly implemented backup systems dramatically reduce post-incident downtime, minimizing financial and reputational damage when something goes wrong. Backup archives provide historical data needed for security investigations, helping you understand how and when systems were compromised.
Perhaps most importantly, in today's ransomware-heavy threat landscape, backups allow complete system restoration to a known-good state after compromise. This capability alone can save your business thousands in ransom payments and weeks of downtime, making it one of the most cost-effective security investments available.
8. Improve Social Media Security With Specialized Tools
Social media security tools monitor your accounts for suspicious activities, including unauthorized login attempts, profile changes, or mass deletion of posts.
For SMBs, these specialized tools automatically flag suspicious emails or messages, eliminating the burden of manual verification in increasingly sophisticated phishing landscapes. They protect your logins, passwords, and sensitive data from malware or keyloggers designed to steal information. When breaches do occur, they provide quick account recovery guidance, reducing downtime and potential damage.
These tools offer centralized security management across all social platforms rather than relying on each platform's native security features, which may be limited or difficult to configure properly. They enable granular control over which employees can access specific accounts and what actions they can perform, limiting potential insider threats. Many scan for sensitive information in posts and messages that might violate compliance requirements or expose business data, preventing accidental leaks.
Advanced tools automatically detect malicious links in comments, messages, and posts targeting your employees or customers, protecting your entire social media community. When incidents do occur, they provide audit trails to understand how breaches happened, helping you improve security and prevent future incidents.
How Spikerz Shields Your Social Media From Digital Threats

Spikerz is a complete social media security platform designed specifically to protect business accounts from the full spectrum of digital threats.
Our platform offers advanced protection through social engineering detection, identifying and blocking sophisticated attempts to manipulate your team. We provide secure content backup, archiving all your social media content for quick recovery after any incident. Our shadowban detection alerts you when platforms limit your content's visibility, helping you address issues before they impact your reach.
Spikerz continuously monitors for impersonator accounts, finding and helping remove fake profiles mimicking your business before they can damage your reputation. Our account recovery assistance provides step-by-step guidance to reclaim compromised accounts quickly. We implement robust bot attack prevention, blocking automated threats before they damage your online presence.
The system continuously scans for suspicious activity, unauthorized access, and security threats, immediately alerting users and taking action to mitigate breaches. Also, our technology detects malicious bots and malware attempting to hijack accounts while monitoring for impersonators and unauthorized content use across the social media landscape.
Additional Benefits Your SMB Will See From Using Spikerz
Beyond core security functions, Spikerz delivers tangible business benefits for SMBs. Our early threat detection and rapid response capabilities minimize disruption, reducing costly downtime that impacts your bottom line
Spikerz simplifies security management by handling monitoring and response externally, reducing the in-house burden on your limited IT resources. With security concerns handled professionally, your team can focus on growth initiatives rather than constant threat monitoring. Our comprehensive protection includes 24/7 monitoring, quick response time, and disaster recovery planning to safeguard against the full spectrum of cyber threats.
We complement our technical protection with extensive educational resources, including guides, blog posts, and chatbot support to help your team navigate security challenges effectively. This knowledge transfer empowers your business to maintain stronger security practices across all operations.
Don't Be The Next Breach Headline
If you haven't upgraded your social media security yet, you're leaving your business's digital front door unlocked. Every day without proper protection is another opportunity for hackers to damage your reputation, steal customer data, and interrupt your operations.
The businesses that survive in today's threat landscape aren't the largest—they're the most prepared. Take the first step toward true security today. Your customers trust you with their data and engagement. Protect that trust with the security solution designed specifically for business social media accounts.
Act now before you become just another cybercrime statistic. Your business deserves better protection.
Conclusion
Digital threats facing SMBs aren't going away—they're multiplying. As we've seen, cybercriminals specifically target small and medium businesses because they expect to find weaknesses. With cybercrime costs projected to reach $1.82 trillion by 2028, the question isn't whether your business will be targeted, but when.
Fortunately, you don't need an enterprise security budget to protect your social media accounts and digital assets. If you implement the practical steps outlined in this guide—from security assessments and employee training to specialized tools like Spikerz—you’ll close the security gaps hackers exploit.
Remember: in cybersecurity, an ounce of prevention is worth pounds of costly recovery efforts.
Take action today to secure your business's digital presence. Your customers, employees, and bottom line will thank you.














